This is a quick guide to Azure Site-to-Site VPN. I am currently preparing my environment for a technical session about Windows Virtual Desktop, I had to establish a connection from my Azure Virtual Network to my On-Premises Network. This is required to make sure that I can join my WVD Hostpool virtual machines to my on-premises domain. To do so, I am going to create a Site-to-Site VPN Connection from Azure to my Get Modern HQ HomeLab. Below an overview of what I want to achieve:

Before you begin, it is important that you have met the following criteria:
- Make sure you have a compatible VPN device and someone who is able to configure it. In this blog post we will use a UniFi Security Gateway.
- Verify that you have an externally facing public IPv4 address for your VPN device, you can get your public facing IPv4 from here: http://getmyipaddress.org/ Important to understand, that whenever you don’t have a fixed public IPv4 address, your Site-to-Site VPN is likely going to crash the moment your ISP renews your public facing IP Address.
- If you are unfamiliar with the IP address ranges located in your on-premises network configuration, you need to coordinate with someone who can provide those details for you. When you create this configuration, you must specify the IP address range prefixes that Azure will route to your on-premises location. None of the subnets of your on-premises network can over lap with the virtual network subnets that you want to connect to.
As I understand that people already blogged about this topic, I have created a step-by-step video about the full configuration, so I will not go very deep into the details. Please find below the high-level implementation steps for our Site-to-Site VPN Connection. Scroll down to the bottom and Check the video (00:05:36) for a hands-on experience:
Create a virtual network
When using a virtual network as part of a cross-premises architecture, be sure to coordinate with your on-premises network administrator to carve out an IP address range that you can use specifically for this virtual network. If a duplicate address range exists on both sides of the VPN connection, traffic will route in an unexpected way. Additionally, if you want to connect this virtual network to another virtual network, the address space cannot overlap with the other virtual network. Plan your network configuration accordingly. Tip! If you are setting this up in a demo environment and you have a DNS Server on-premis, make sure you configure your DNS. In the video (00:01:37) you can see where to configure your local DNS. If not, you won’t be able to resolve your on-premises domain.
Create a Virtual Network Gateway
Creating a gateway can often take 45 minutes or more, depending on the selected gateway SKU.
The virtual network gateway uses specific subnet called the gateway subnet. The gateway subnet is part of the virtual network IP address range that you specify when configuring your virtual network. It contains the IP addresses that the virtual network gateway resources and services use.
When you create the gateway subnet, you specify the number of IP addresses that the subnet contains. The number of IP addresses needed depends on the VPN gateway configuration that you want to create. Some configurations require more IP addresses than others. We recommend that you create a gateway subnet that uses a /27 or /28.
If you see an error that specifies that the address space overlaps with a subnet, or that the subnet is not contained within the address space for your virtual network, check your VNet address range. You may not have enough IP addresses available in the address range you created for your virtual network. For example, if your default subnet encompasses the entire address range, there are no IP addresses left to create additional subnets. You can either adjust your subnets within the existing address space to free up IP addresses, or specify an additional address range and create the gateway subnet there.
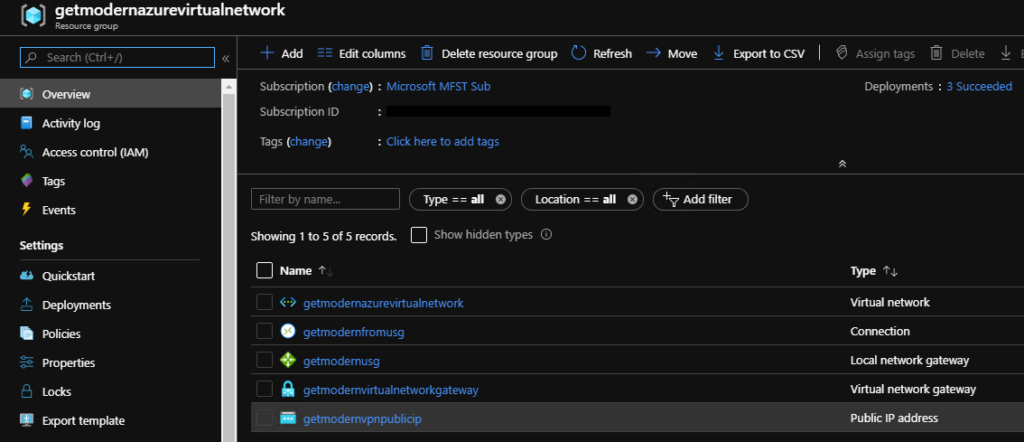
After the gateway is created, you can view the IP address that has been assigned to it by looking at the virtual network in the portal. The gateway appears as a connected device.
When working with gateway subnets, avoid associating a network security group (NSG) to the gateway subnet. Associating a network security group to this subnet may cause your Virtual Network gateway(VPN, Express Route gateway) to stop functioning as expected. For more information about network security groups, see What is a network security group?
Add a connection to the Virtual Network Gateway
In this step we are going to create our Site-to-Site VPN connection between our azure virtual network gateway and the on-premises UniFi Security Gateway.
Create and Add a local network gateway to the connection
The local network gateway typically refers to your on-premises location. You give the site a name by which Azure can refer to it, then specify the IP address of the on-premises VPN device to which you will create a connection. You also specify the IP address prefixes that will be routed through the VPN gateway to the VPN device. The address prefixes you specify are the prefixes located on your on-premises network. If your on-premises network changes or you need to change the public IP address for the VPN device, you can easily update the values later.
Check the video below for the configuration steps:
I hope it helps, see you next time!
Cheers!
Ken